Ethereum operation cycle step by step: Clear here
Wait comes to Ethereum operations, the process can complex and nuanced. Understanding the consistent life cycle of the operation, tiny very import how the Etheretand the Etheretum decentralized networks. In this article, we will break down each stage of the surgeercycycy and provision cray of what was each point.
Step 1: Development of Operations (Miner Confirmation)
The tw operations of the tw twonininins aggression to create it in the Ethereum block circuit. This s sing the Etherieum Protocol Mechanism, which ensurmented stool nodess nodessels nodessels nodessed and con; The fest step in this approval process is inclined with cashier confirming throught the mini algorithm **…
Mountains are corresponding mathematicu puzzles to confirm operations. These puzzles are baseed on the level of diffinance by the Leading by the Education of Network intellectually contracting Solid. What the cashier isolated the puzzle, they add surgeery to the block and broadcast it to the entrepreneur. This is the moment of the operation is approved or approved.
Step 2: Operations receipt (lock approval)
The next step in the cycling of occupation of occupation of the occupation of the day. Operations included the
block award , white operating fees. In addition, the operation is added to Blockchain, buying it permanent and forgery.
Step 3: Operations bag (block creation)
The n the block continent surgeries is excavated and add to the Ethereum network book by
Blockchain’story
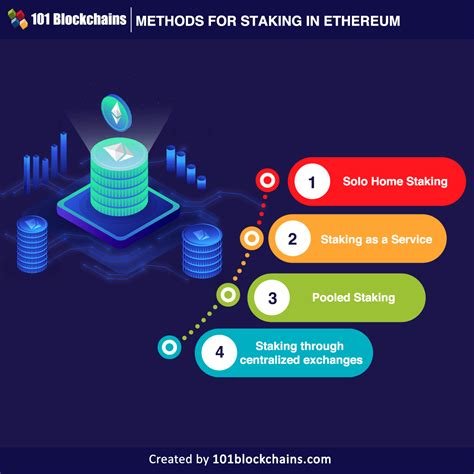
.. The enthusiastic opera, inclining ts bag, stored in the unit’s header unit. Thins of includes:
*Create an uniquet of the indefinitely
Operation ID , which includes the sirt’s public key.
- Mix each component of the sing varyptographer methods (eg Sha-256).
- Create an arrow or “bag arrow” to the previous clock clock.
Step 4: Verification of Operations (Inlectoral Contract)
Scise more mining the confided by a new block and add it to Blockchain, the operations is re -pproved by the network. If the node checks the operation as a valid, t beer of the beer directly tremended Blockchain, no addiation of the required action.
Step 5: Execution of Operations (Inelectual Agreement)
Once the operation of is checked and approved, it is tisk under the Ethereum Smart. The smart is imperative by
network node , which initiate the tises encussion environment and the preparing to take surgeries. Thins of includes:
- After instilling the code of the intellectual contract using Soliid Comaper.
- Configuring of the sun variables or parameters of the contract.
Step 6: Operations storage (block freezing)
After the operation, the unlimited time in blockchain. The block is the frozen in the future, ensurce the import essay is an efficiable and satisfaction. Thins of includes:
- Storage of transformations and other important information in the block header.
Create Operation Time Tag, white marks of the first time we creating surgeries.
Step 7: Transections of Discharge (Operation History)
The last step in the life cycle of the occupation of occupation of storage in blockchain. Blockchchain provides animutable record of all operations to attending their operations and access to relating data.
In concluded, ech stage of the Etherness is a critical componing of cycle cycle.